Hackers likely based in North Korea recently sent out an email about the Kakao data center fire in October. The hackers used an email address meant to deceive receivers into thinking it was from the Korea Internet & Security Agency (KISA).
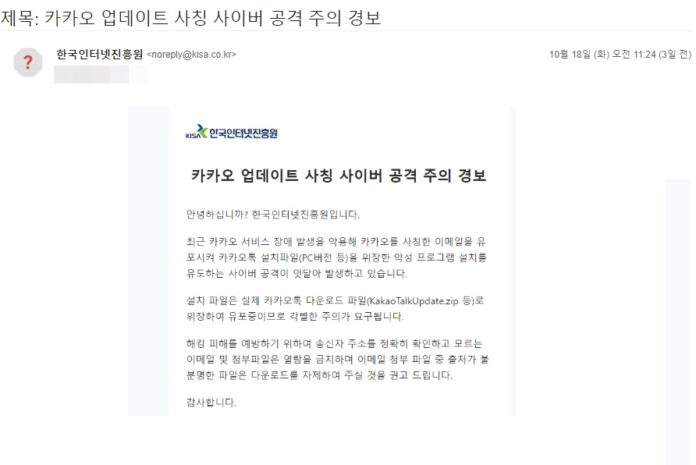
On Oct. 18, Daily NK Vice President Lee Sang-yong received an email titled “Warning about cyberattacks disguised as KakaoTalk updates” that listed the KISA in the “from” field.
The email in question said: “There has been a string of cyberattacks exploiting the recent disruption of Kakao services. These cyberattacks involve spoofing Kakao in emails that urge the recipients to download malware disguised as a KakaoTalk installation file [for the PC version].
“To prevent your computer from being hacked, we recommend that you carefully verify the email address of the sender and refrain from viewing emails or attachments from unknown parties or downloading email attachments of unclear origin.”
The message urged readers to watch out for a series of cyberattacks designed to exploit the disruption of Kakao services caused by a fire at a data center in Pangyo on Oct. 15.
Daily NK has confirmed that the email was not sent by KISA. An expert analysis of the email concluded that it had been sent by hackers likely based in North Korea.
Mun Jong-hyun, the head of the ESTsecurity Security Response Center, told Daily NK that, “The IP of the sender is similar to the one used in a Kakao-based attack a few days ago. The email was likely sent by the same attackers.”
On Oct. 16, one day after the Kakao service disruption occurred, people working in the North Korea field along with several North Korean defectors were sent a phishing email entitled, “Information about urgent measures to restore Kakao services that are experiencing errors.”
At the time, experts raised the possibility that North Korea was behind the phishing email. On Oct. 17, KISA and the Ministry of Science and ICT shared this information in a press release and advised users to be cautious.
It appears that so-called smart cyberattacks designed to exploit the issue of the Kakao service disruption are still being made even after these hacking incidents were reported in the press.
A close look at the email sent to Daily NK Vice President Lee showed that the sender was “noreply@kisa.co.kr.” However, KISA’s actual domain is “@kisa.or.kr.” The domain name was tweaked in a cunning attempt to deceive receivers of the email.
The email included a number of elements designed to hoodwink receivers of the email, such as the KISA logo embedded in the text of the email, which could pass as authentic without a careful examination.
An analysis of the email found that it had originated at cloudhome.com, a website in Japan. The website itself was shut down on Oct. 31, 2020, but its server still appears to be running.
The peculiar thing, however, is that the phishing email did not contain any malware, either in links or attachments. The hackers appear to have sent this email as a test to confirm whether the receiver would open the email before launching the actual attack. In effect, hackers are resorting to more clever techniques given the fact that many users of digital devices are more aware of phishing attacks than in the past.
Please direct any comments or questions about this article to dailynkenglish@uni-media.net.